It's dangerous to allow unmanaged personal devices access to the corporate network but due to the remote work shift there are many Australian organisations in this situation. What should they do?
The Covid-19 pandemic is now into its ninth month in Australia and yet many organisations are still rolling the dice and allowing remote workers to access corporate networks from unmanaged personal devices.
These devices can include mobile phones, laptops, tablets, desktops, USBs and some employees are also using personal WiFi internet connections to access the corporate network.
What are the risks of unmanaged personal device access?
The rise in unmanaged network-connected devices increases the attack surface of the enterprise and allows cybercriminals to capitalise on the weakest link - the user endpoint - to gain a foothold into the network.
If compromised devices on the network go undetected, they can be used as launch pads to target higher-value assets, gain access to sensitive information, and cause significant business impact.
The biggest security risks associated with unmanaged devices are
- IT lack of visibility of unmanaged endpoints and inability to enforce security protocols
- Employee lack of commitment to security practices and risky behaviour exposing the network
The outcome of these two risks is an increased likelihood of a cyber security incident which could involve lockdown or loss of corporate data, resulting in significant financial and reputational loss.

How much of a risk are unmanaged endpoints really?
- 36 percent of Australian workers say they often or always use personal devices like mobile devices and computers to access corporate data
- 41 personal of Australian workers surveyed did not have basic password protection on all of their personal devices
- 49 per cent of Australian remote workers have IoT devices connected to their home network, eight per cent using lesser-known brands
Even remote workers with corporate devices, behave in ways that threaten the security of the network including
- 68 per cent of Australian remote workers connect corporate laptops to the home network
- 80 percent of remote workers use their work laptop for personal browsing
- 56 percent of employees have downloaded a non-work application onto their corporate device
What is the answer to protecting against unmanaged endpoints?
Banning all unmanaged devices from accessing the corporate network is unlikely to be a realistic option. A risk-based approach is needed to select and apply different levels of visibility and control.
Ultimately the challenge is to bring a level of visibility and control to unmanaged devices, and safely enable their use.
To achieve this, a process is needed to find devices that are not secured, appropriately control their connections,
monitor their traffic and behavior, and block any malicious behavior.
All of this needs to be done in the context of how a device is used so that only the actions and privileges that are required to support the business are sanctioned.
Four Steps to Address Unmanaged Network Access
For corporate-owned devices, the simplest way to address the issue could be to apply the combination of a Unified Endpoint Management (UEM) agent to the endpoint; and a Mobile Threat Defence solution across the endpoint, application management and the network.
However, for personally-owned devices, it is unlikely that end users will agree to, or reliably enable, the installation of an endpoint agent. So what to do? Here are the four steps to navigate:
Step 1. Automate discovery of all unmanaged devices
Establishing visibility is a critical first step. You can't manage what you can't see. Having a complete asset inventory of all devices on the network is a critical foundation for an effective security solution. Given that unmanaged devices can be transient, such as a device introduced by an employee or contractor, it is important that the device discovery process is both continuous and automated.
Step 2: Profile acceptable behaviour
Once a device is visible, the next step is to understand what it is doing and whether the actions are acceptable. This means observing device behaviour over time to establish baselines, and comparing observed behaviour to other devices of a similar type or functional role. This profiling should include an understanding of common network connections, protocols in use and other typical behaviors. This phase is also critical for understanding how a device is used in the enterprise, so that we can establish appropriate policies that truly enable the device and the business.
Step 3. Establish and enforce appropriate behaviour
Next, is to proactively control the attack surface presented by unmanaged devices. This will require the organisation to establish sanctioned behaviours based on the type of device and its role. At a high level, this means setting what is allowed, and denying the rest.
Step 4. Identify and stop malicious behaviour
Having identified and enforced approved behaviour, the next step is to identify malicious behaviour. As well as identifying the signs of malicious tools and techniques, it is also necessary to monitor for signs that a device may be compromised. Once a threat is identified, there needs to be in place the ability to block the threat automatically. If a device is acting as an exfiltration channel of the network, we obviously need to stop the flow of data automatically in order to mitigate damage.
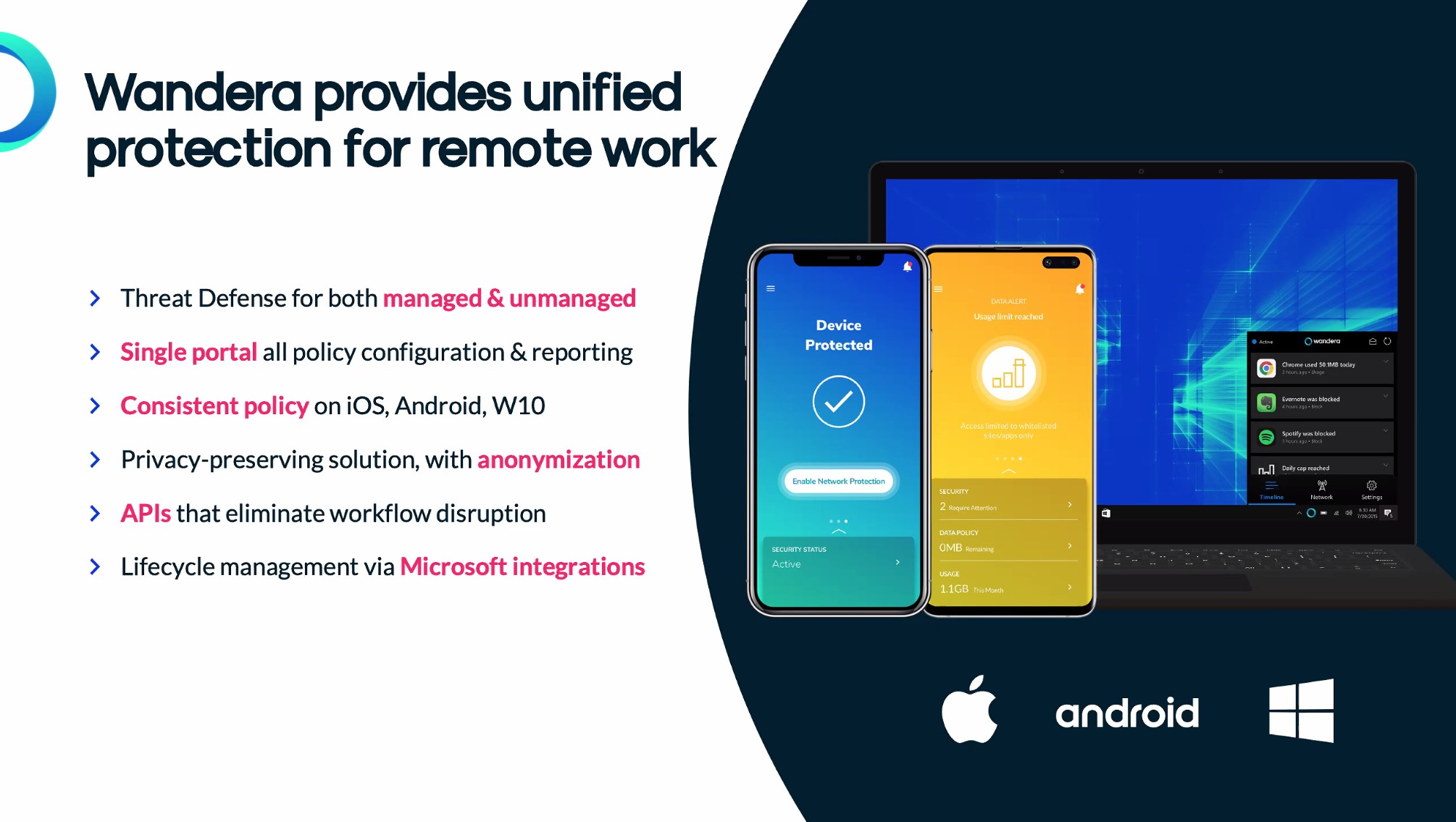
Consider MobileCorp and Wandera to 'manage the unmanaged'
MobileCorp is an Australian ICT services company who assists enterprise and business to solve mobility issues. We recommend Wandera as an excellent product to manage the unmanaged devices on your network.
Wandera delivers unified cloud-based endpoint, application and network security for enterprises including private network access and mobile threat defence.
The company, which has an Australian office, has been highlighted in two Gartner Market Guides in 2020 for zero trust network access and for mobile threat defence.
Two key features of Wandera are:
- Zero-Trust Private Network Access
Moving beyond the device to enforce security at the application and network layers, Wandera offers granulated network protection by applying a zero-trust access policy. This is particularly important in the Covid remote working era as it provides users with the flexibility to work any time, anywhere with secure remote access – for unmanaged and BYOD devices. - next-gen encryption and networking protocols
- identity-based micro-tunnels secure your corporate apps
- protect sensitive data with adaptive access such as device risk posture and location
- integrate IdP and UEM for enhanced management, or SIEM and SOAR for greater visibility
- zero latency issues by eliminating unnecessary traffic backhauling
- silent device authentication or seamless access via SSO
- avoids requirement to re-authenticate every time
- configure least-privilege access for applications individually with granular controls
- review security with real-time event visibility and easily audit logs

- Threat Detection and Defence
Protect against all cyber threats, from device vulnerabilities to phishing to malicious or risky apps, with multi-level cloud and endpoint security. Manage risks with zero-day advanced threat intelligence- monitor endpoints for vulnerabilities, from escalated privileges to outdated OS's
- perform continuous app risk assessments for advanced detection of malware and risky applications
- detect man-in-the-middle attacks and open a fail-safe VPN tunnel to ensure business continuity
- protect against known and zero-day phishing threats
- stop malicious downloads and connections to third-party app stores. Prevent data ex-filtration and command-and-control attacks
- monitor for data leaks and prevent sensitive data loss. Safeguard user privacy with added encryption
e. phill.mcsherry@mobilecorp.com.au
m. 0419 173 333
About MobileCorp
MobileCorp is an enterprise ICT solutions company with a mission to deliver our customers a communications technology edge. We provide Managed Mobility Services, Enterprise Mobility Management, Complex Data and IP Networks, and Unified Communication solutions. We have a proven track record providing managed services for Australian enterprise and business, and we are a Telstra Platinum Partner.
UEM Michelle Lewis 13 Oct 2020
Related Posts
Popular Tags
- Mobile Devices (78)
- Mobility (70)
- Telstra (61)
- MobileCorp Managed Services (52)
- 5G (50)
- Mobile Network (33)
- Apple (30)
- Cradlepoint (30)
- MobileCorp (30)
- iPhone (26)
- Remote Working (23)
- Networks (21)
- Network (17)
- Covid-19 (16)
- UEM (16)
- Mobile Security (15)
- Wireless WAN (13)
- Cyber Security (12)
- MDM (12)
- TEMs (9)
- Unified Comms (9)
- Cloud (8)
- Mobile Expense Management (8)
- Wandera (8)
- Mobile Device Lifecycle (7)
- Mobile Device Management (7)
- Android (6)
- Data Networks (6)
- Sustainability (6)
- Samsung (5)
- Digital Experience (4)
- IOT (4)
- Microsoft Intune (4)
- Network Security (4)
- Security (4)
- Unified Communications (4)
- Microsoft (3)
- Data (2)
- Government (2)
- Managed Desktops (2)
- Microsoft 365 & Teams (2)
- nbn (2)
- webinar (2)
- Blog (1)
- EMM (1)
- Emerging Technologies (1)
- IT Services (1)
- Retail (1)
- SD-WAN (1)
- Starlink (1)
- Telstra Services (1)
- video (1)






